New DoS Vulnerability Found in Ruby’s cgi.rb
The official Ruby language homepage is reporting that another DoS vulnerability has been found in Ruby's CGI library (cgi.rb). The solution is to upgrade to the newly released Ruby 1.8.5-p2 (warning: direct link to .tar.gz file). Specifically:
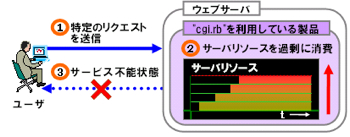
A specific HTTP request for any web application using cgi.rb causes CPU consumption on the machine on which the web application is running. Many such requests result in a denial of service.
(source: ozmm)




December 5, 2006 at 1:38 pm
It looks like another MIME-parsing bug, just like the last one. The Japanese disclosure page just says that a DoS is possible by sending a carefully-crafted request, so I looked at the code: the only change in 1.8.5-p2 is that the MIME boundary read from the header is now escaped before being interpolated into the boundary-matching regular expression. Previously, the header was interpolated directly.
I've been trying to recreate the error, but I haven't succeeded so far. I can't find any details about 1.8.5-p2 on any of the English or Japanese mailing lists, either.
December 5, 2006 at 3:13 pm
I couldn't make hide nor hair of it, to be honest, so I am glad there are people who are looking into it in more depth :) I'm just trusting the official Ruby site.
I did think that Japanese graphic was pretty cool though..!
December 5, 2006 at 4:50 pm
I think this is the same as this? http://rubyforge.org/pipermail/mongrel-users/2006-October/001946.html
Talk about slow response time?
December 5, 2006 at 6:17 pm
Jon, that's a separate issue that's fixed by a previous patch.
This is a new, related vulnerability, with a different patch.
December 5, 2006 at 7:01 pm
But the two patches ([1] and [2]), as far as I can tell, modify exactly the same line in exactly the same way?
[1] http://rubyforge.org/pipermail/mongrel-users/attachments/20061025/09b5f29a/attachment-0001.obj
[2] http://ftp.ruby-lang.org/pub/ruby/1.8/ruby-1.8.5-cgi-dos-1.patch
December 6, 2006 at 12:24 am
Jon: Yeah, like Paul says, I think this is a separate issue. On the official Ruby site, at least, they say it's not the same as the Oct/Nov issue. I think this might be why it's at 1.8.5-p2, since p1 probably solved the initial one.
Seems like cgi.rb could do with a nice audit :)
December 6, 2006 at 12:27 am
Jon: Oops.. my response just above was made before I saw and moderated your 7:01pm comment :) Interesting find! I must confess I have not downloaded the latest version to check it out, but it does say this:
Please note that the previous patch (http://ftp.ruby-lang.org/pub/ruby/1.8/ruby-1.8.5-cgi-dos-1.patch>) does not fix this problem.
December 6, 2006 at 11:11 am
OK, let's clear up the confusion! There are now three versions of Ruby 1.8.5:
* 1.8.5
* 1.8.5 + ruby-1.8.5-cgi-dos-1.patch (we could call this 1.8.5-p1)
* 1.8.5-p2
Jon's links 1 and 2 are indeed the same patch for the same flaw. This new one is different, though.
If you download 1.8.5, apply the first patch, and then diff cgi.rb against that from 1.8.5-p2, you'll see three further lines of changes[1].
1. http://po-ru.com/files/ruby-1.8.5-cgi-dos-2.patch
December 6, 2006 at 12:01 pm
Thanks Paul, just what we needed :)
December 6, 2006 at 11:13 pm
Paul: Ahah, thanks very much for clearing that up.